This endpoint is also configured with a denyall access rule and should be secured consciously.
Spring cloud security oauth2 jwt.
Previously the spring security oauth stack offered the possibility of setting up an authorization server as a spring application.
A declarative model which can be heavily configured externally or centrally lends itself to the implementation of large systems of co operating remote components usually with a central indentity management service.
Spring cloud gateway can forward oauth2 access tokens to the services it is proxying.
Spring cloud security offers a set of primitives for building secure applications and services with minimum fuss.
In this chapter you will learn in detail about spring boot security mechanisms and oauth2 with jwt.
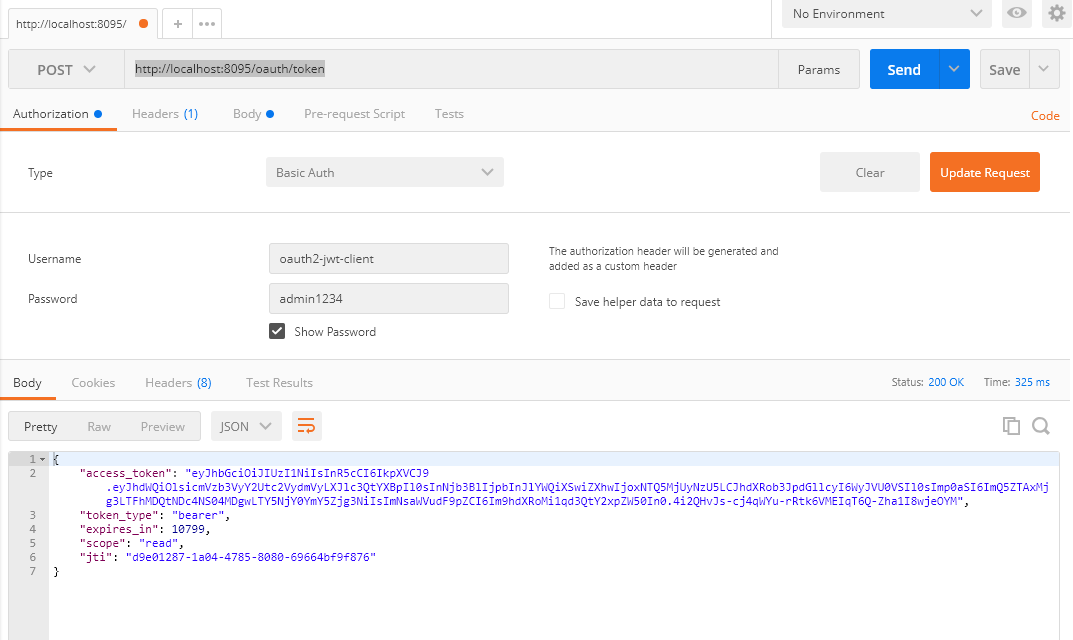
In this example we will use json web token jwt as the format of the oauth2 token.
Oauth2 is an authorization framework that enables the application web security to access the resources from the client.
In addition to logging in the user and grabbing a token a filter extracts the access token for the authenticated user and puts it into a.
Without going much into theory let s assume a real world security problem statement and see how we can accomplish our desired solution using jwt json web token oauth2 security features.
We then had to configure it to use jwttokenstore so that we could use jwt tokens.
Integrating the uaa with spring cloud gateway.
The spring security oauth library also configures a oauth check token endpoint which validates and retrieves the decoded jwt.
The spring oauth 2 0 authorization mechanism manages and verifies the oauth 2 0 tokens.
However the oauth stack has been deprecated by spring and now we ll be using keycloak as our authorization server.
This sample was developed partly based on the official sample of spring security oauth 2.
These tokens are then used to access the protected resources.
Spring cloud security 为构建安全的springboot应用提供了一系列解决方案 结合oauth2还可以实现更多功能 比如使用jwt令牌存储信息 刷新令牌功能 本文将对其结合jwt使用进行详细介绍 jwt简介.