Masquerader individual who is not authorized to use the computer and who penetrates a systems access controls to exploit a legitimate users account.
Types of computer security ppt.
The powerpoint ppt presentation.
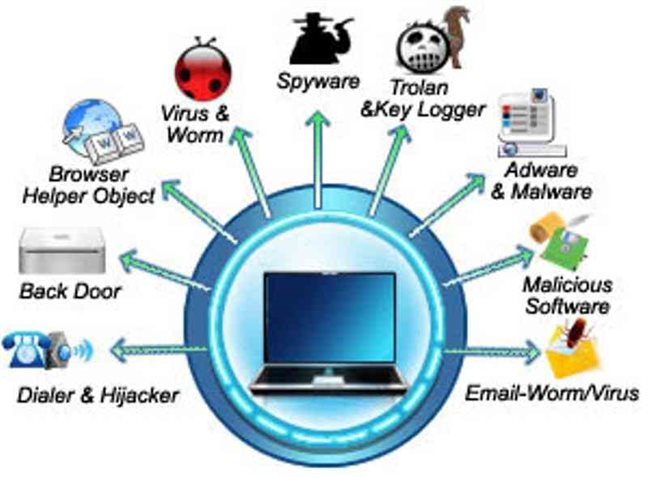
Computer security threats are relentlessly inventive.
What is computer security.
So computer security involves controlling our physical access as well as protecting against the harm that occurs via network access data.
Computer security is one of the most important issues in organizations which cannot afford any kind of data loss.
With a lot happening on the web it becomes an utmost need to secure the content from loss and interception as there hovers a constant vision of malice to disrupt the.
Computer security is a branch of computer technology known as information security as applied to computers and networks.
Devices tools techniques and methodologies used to secure the network.
Computer security is the property of its rightful owner.
Institutional data security congratulations.
Types of computer security.
Threats and protection techniques.
In short anyone who has physical access to the computer controls it.
You are elected member of the newly established computer and data security team in your institution.
Arm yourself with information and resources to safeguard against complex and growing computer security threats and stay safe online.
Computer security or it security is a global demand to protect our computer systems from the malicious attackers from doing any damage to our hardware software as well as disruption of the services provided.
Passwords hidden files and other safeguards can t keep out a determined attacker forever if he can physically access your computer.
1 make a list of all possible risks that can have an impact on the security and stability of your data and internal and external information technology services.
Computer security means the protection of computing systems and the data that they store or access.
In this type of mitm attack an attacker hijacks a session between a trusted client and network server.
Here are some common types of man in the middle attacks.